Table of Contents
Google Cloud Is 100% Secure, Is It?
Google Cloud is an extremely secure environment, there is no doubt about that. But here is a sad fact. Despite the robust security measures implemented by Google cloud developers, departing employees continue to pose a cybersecurity threat. While Google itself offers extensive tools to safeguard company data, the human element remains a critical vulnerability.
One of the reasons for this is that employee off-boarding and data archiving, the process of securely removing a former employee’s access to company systems (a part of IAM procedures), is often overlooked or deprioritized in many organizations. This is easily explainable, as businesses tend to focus on onboarding new employees and maintaining daily operations, leaving offboarding as an afterthought. However, this neglect can lead to serious security breaches, particularly within platforms like Google Workspace, where seamless access management is crucial.
Let’s investigate, what are the real-world implications and actual risks of improper offboarding.
Statistics on Data Leaks from Improper Offboarding
— Most companies do next to nothing while offboarding users
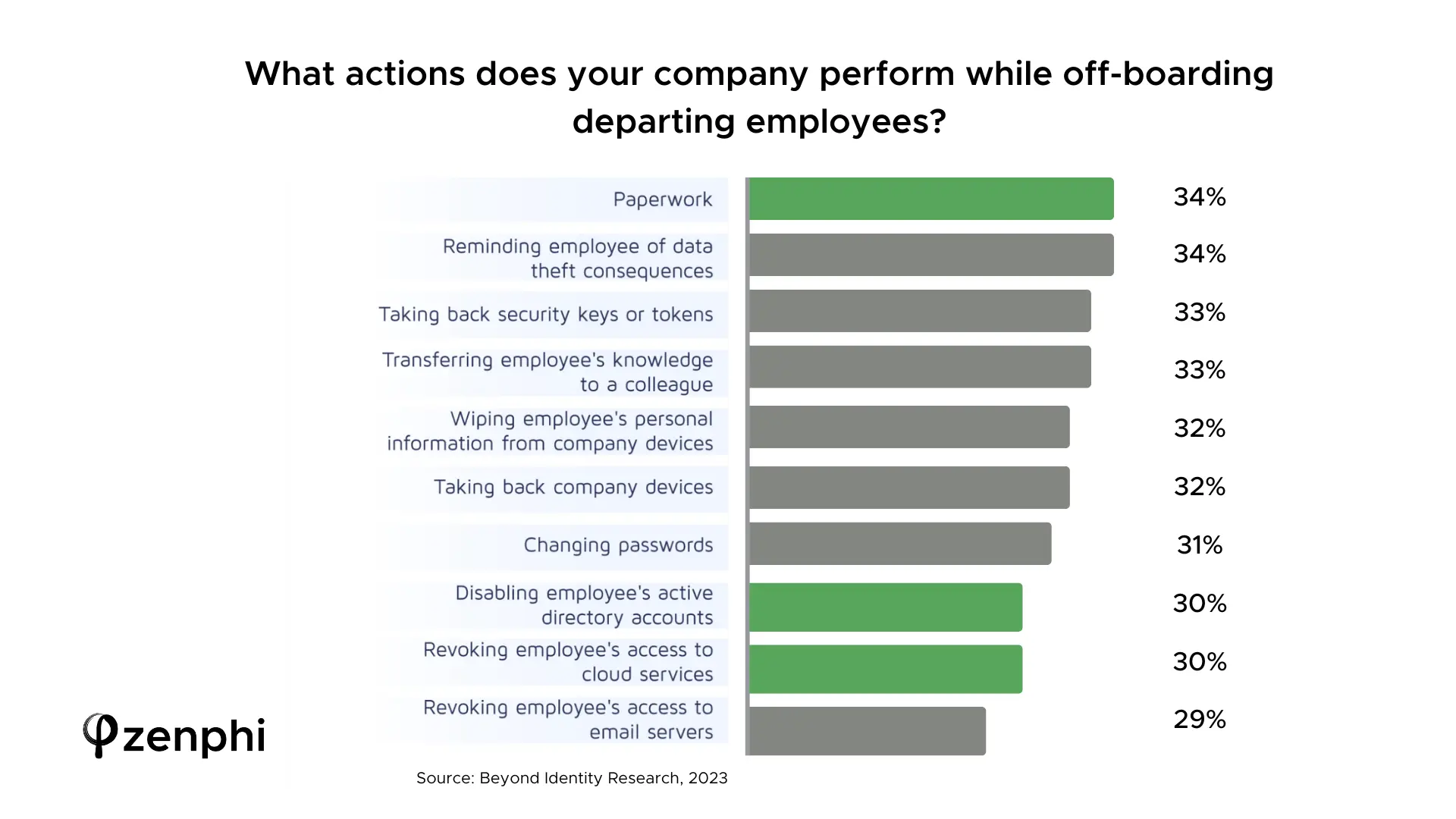
According to Beyond Identity research, conducted in 2023, nearly one-third of businesses have experienced data breaches due to ineffective offboarding. This often involves former employees retaining access to company systems and data, leading to significant security vulnerabilities. Shocking fact: only 29% of companies revoke employee’s access to email servers, while most companies limit their offboarding activities to paperwork.
— 90% of ex-employees still can access company’s data
The same research revealed another telling fact: a staggering 91% of employees reported still having access to company files after offboarding. There is little doubt that this lapse can result in unauthorized access and potential data theft or loss.
— Offboarding neglect results into huge financial and reputational losses
Morgan Lewis’s fresh study conducted in 2024, discovered that the average cost of a data breach in the U.S. is approximately $9.44 million. In addition to financial losses, companies can suffer severe reputational damage, with over 25% of businesses reporting harm to their reputation due to improper offboarding practices.
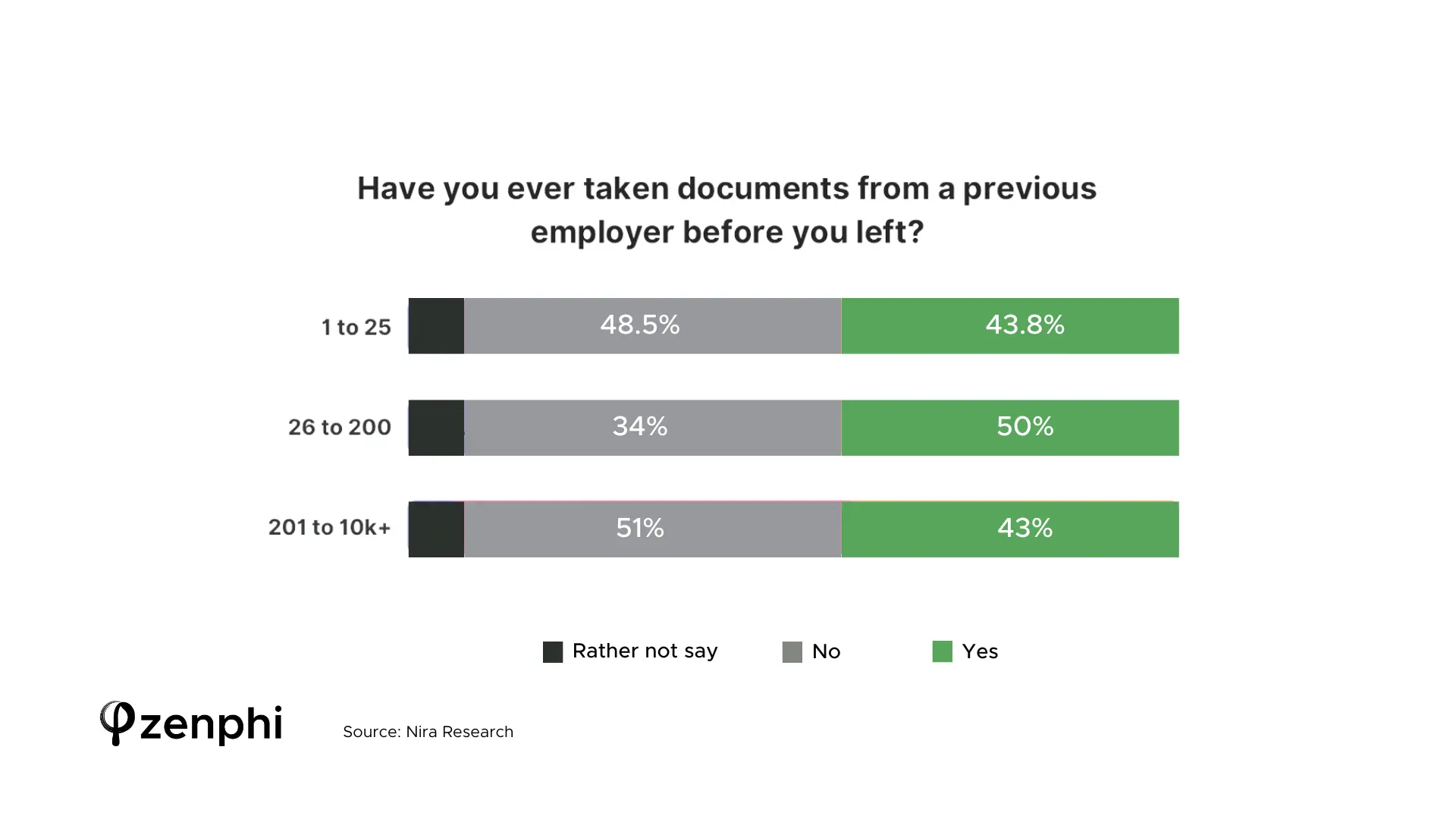
— 45% Of Employees Actually Take Company’s Data With Them When Leaving
Nira’s research discovered that a shocking number of employees admit to using data of their ex-employer. Almost half – 45% of people – were willing to admit that they’d taken documents from the company they used to work for.
Real-World Examples of Data Breaches Due to Improper Offboarding
But hold on! Statistics are great but what about the real threats? If the majority of companies don’t have protocols for offboarding, it doesn’t automatically mean that they all become victims of data leaks, does it? Let’s look closer at some real-world examples of ex-employees steeling company’s data: something that you should definitely consider working on your Google cloud IAM policy.
Pagosa Springs Medical Center (PSMC)
In 2018, PSMC faced a major HIPAA violation, costing them $111,400, due to improper offboarding of a terminated employee. The former employee retained access to PSMC’s web-based scheduling calendar, which contained patients’ electronic protected health information (ePHI). This oversight led to unauthorized access and a significant compliance breach (JumpCloud).
Tesla
In early 2021, Tesla experienced an internal data breach when a software engineer, Alex Khatilov, allegedly stole files related to Tesla’s Warp Drive software system. He moved the files to his personal Dropbox account. Tesla discovered the incident and promptly terminated his employment and pursued legal action against him (CurrentWare).
Royal Canadian Navy
Sub-Lieutenant Jeffrey Delisle of the Royal Canadian Navy was convicted of passing secret military information to the Russian Embassy. He used his access to steal data and sell it for financial gain, highlighting the severe risks posed by disgruntled or financially distressed employees with access to sensitive information (CurrentWare).
Impact on Offboarding Protocols On Cybersecurity
As you can see yourself by analyzing the facts above, despite the relatively low prioritization, the risks associated with improper offboarding are substantial. Former employees with lingering access can lead to:
- Data Breaches: Unauthorized access to sensitive information can result in data theft, leaks, and significant financial and reputational damage.
- Compliance Violations: Failure to revoke access promptly can lead to violations of regulations such as GDPR and HIPAA, resulting in hefty fines.
- Operational Disruptions: Former employees with access to systems can disrupt operations, whether intentionally or unintentionally.
- Financial & Reputational Losses: Company’s whose former employees still have access to sensitive data, face very real risk of litigation and financial losses.
Google Cloud IAM Best Practices: How To Prevent Data Leaks That Can Be Potentially Caused By Departed Employees
If your company uses Google Workspace, the risk of potential losses due to improper offboarding can be significantly reduced with just a few simple steps.
By automating the employee offboarding process, you can ensure consistency, compliance, and adherence to high cybersecurity standards. With Zenphi, the #1 Google Workspace workflow automation tool you can easily create a process to offboard departing employees, revoke their access to Google Drive, log them out from all devices, and change their credentials to secure your systems. Watch this video tutorial or read this article on automatically revoking employee access during offboarding.