Discovering seven essential automations that Google Workspace administrators should consider implementing this year.
Table of Contents
Leveraging Automation For Google Workspace MDM In 2025
As organizations continue to expand their reliance on digital ecosystems, managing devices in Google Workspace becomes increasingly complex and critical. For 2025, leveraging automation in Mobile Device Management (MDM) is not just an option; it’s a necessity for ensuring security, compliance, and efficiency.
On the other hand, leveraging automation promises a number of positive outcomes every Google Workspace administrator should aim for:
- Enhanced Efficiency: Automation speeds up numerous MDM-related tasks such as device provisioning, software updates, and security checks.
- Reduced Errors: Manual processes are prone to errors, which can lead to security vulnerabilities or non-compliance with policies. Automation minimizes these risks by standardizing processes and eliminating the variability introduced by human intervention.
- Improved Compliance: With stricter data protection regulations, ensuring every device complies with legal and corporate standards is paramount. Automation helps maintain compliance by consistently applying the necessary policies and immediately addressing any deviations.
- Scalability: As you company grows, the number of devices under management can increase exponentially. Automation makes scaling easier by enabling the management of a large fleet of devices without proportionately increasing the workload on IT staff.
Seven Must-Have Google Workspace MDM Automations For 2025
1. Automated Device Provisioning
Automate the setup and provisioning of new devices as soon as they are enrolled in Google Workspace. This can include installing necessary apps, configuring Wi-Fi settings, and applying security policies, ensuring that devices are ready for immediate use.
Tools to Use for Automated Device Provisioning in Google Workspace
Google Admin Console — allows administrators to set up basic provisioning templates for Chrome OS devices and mobile devices that connect to Google Workspace. This includes pre-configuring network settings, enforcing security policies, and pushing specific configurations to devices as they come online.
Google Endpoint Management — offers more detailed control over Android, iOS, and other devices, including app management, account setup, and advanced security configurations.
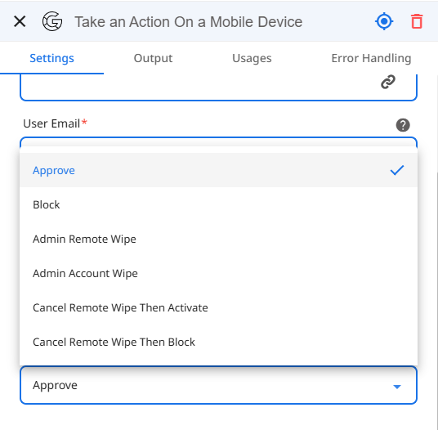
Zenphi — allows to automatically provision devices as a part of the employee onboarding process. With Zenphi, automating Google Workspace MDM workflows and taking actions on the devices is as easy as just choosing an option from a drop-down list.
Zenphi is named the #1 Google admin tool by thousands of your peers. Contact our team to learn how to automate new hire onboarding including device provisioning step, as well as any other steps that you believe are relevant to your particular use case.
2. Conditional Access Controls Automation
Implement dynamic user access control in Google Workspace that adjust permissions based on factors such as device compliance, location, or time. For example, restrict access to sensitive data for devices that do not meet security standards or are outside the corporate network.
Tools to Use for Automated Conditional Access Controls
Google Workspace Security Settings — allows administrators to set basic conditional access policies, such as requiring 2-step verification for accessing certain data or using context-aware access to control access based on user identity and the context of their request. Use the security settings in the Google Admin Console to configure rules based on user groups, IP addresses, and required security postures.
Google Context-Aware Access — Offers more detailed conditional access settings, allowing administrators to create policies that evaluate the context of a sign-in attempt or a resource request before granting access. Set up access levels in Google Admin Console that consider factors like user location, device security status, and the time of access requests.
Zenphi — extends the capabilities of Google Workspace by automating the enforcement of conditional access based on custom workflows. This includes actions like notifying administrators, applying temporary restrictions, or automating compliance procedures if anomalies are detected.
Ready to simplify your Google Workspace access management? From automating RBAC and access approvals to setting up deprovisioning workflows and alerts, this checklist will guide you step by step to ensure your processes are secure and efficient.
3. Security Compliance Checks
Regular security compliance checks are crucial for ensuring that all devices in an organization adhere to updated security standards. Automating these checks can help identify non-compliance issues early, enabling proactive remediation to protect the network and data.
Tools to Use for Automated Security Compliance Checks
Google Admin Console — provides basic tools for monitoring device compliance, such as checking if devices have the latest security patches or if they comply with established security configurations.
Zenphi — can automate the entire process of compliance checks and the subsequent workflows triggered by compliance results. This includes not only identifying non-compliant devices but also taking specific actions like sending notifications.
Third-party Compliance Management Tools (e.g., Symantec, McAfee) — offer advanced compliance monitoring and management features that can integrate with Google Workspace. They provide comprehensive insights into device health, security posture, and compliance with both internal policies and external regulations.
4. Automate Lost or Stolen Device Response
Set up automated workflows to immediately lock and wipe lost or stolen devices, protecting sensitive information. These workflows can also include steps for notifying the user and IT staff, and logging the incident for audit purposes.
Tools for Implementing Lost or Stolen Device Responses in Google Workspace
Google Admin Console — basic functionalities to remotely lock or wipe devices registered under Google Workspace. This can be done manually by administrators once a device is reported lost or stolen.
Third-party Security Tools (e.g., Lookout, Prey) — specialize in device security and can often provide more detailed monitoring, tracking, and automated response options than built-in Google tools. They can help in not only locking and wiping the device but also in attempting to locate the device or capture photos of the possessor.
Zenphi — excels in automating workflows, including those needed for immediate response to lost or stolen device reports. It can orchestrate multiple actions like device locking, data wiping, notifying relevant personnel, and logging the incident for compliance and auditing.
5. Automate Alerts for Unusual Activity
Use machine learning models to monitor devices for unusual activity indicative of security threats, such as multiple failed login attempts or unauthorized access to restricted apps. Automate alerts and initiate predefined security protocols without human intervention.
Tools for Implementing Alerts for Unusual Activity in Google Workspace
For large enterprises: Google Workspace Security Center & Google Cloud Security Command Center — both tools offer insights into security analytics and have alerting capabilities for unusual activities based on predefined rules, such as repeated login failures or suspicious app installations. Google Cloud Security Command Center is compatible with organizations using Google Cloud and integrates machine learning to identify threats more effectively.
For medium-sized companies: Standard Google Admin Console Features or Zenphi — Google Admin Console includes basic device management, user security settings, and simple alert policies. If those are not enough, consider getting more advanced capabilities with Zenphi’s automations. It can be a valuable tool for automating responses to security incidents and managing routine security tasks, even without integrating with more sophisticated security centers. Zenphi will help streamline security protocols by automatically handling tasks like user notifications, password resets, and basic compliance checks.
6. Automated Software Updates
Automating software updates is crucial for maintaining device security and functionality, ensuring all devices in an organization run the latest software versions with the latest security patches and feature enhancements. Automation helps manage updates more efficiently, especially in larger environments, by scheduling updates during optimal times and handling exceptions automatically.
Tools for Implementing Automated Software Updates in Google Workspace
Google Admin Console — allows administrators to manage updates for Chrome OS devices directly within the console. This includes setting policies for when and how updates should be applied.
Third-party Update Management Tools (e.g., ManageEngine Patch Manager Plus, Automox) — offer comprehensive patch management solutions that can be integrated with Google Workspace to extend capabilities beyond native features, especially useful for managing non-Google software on devices.
Zenphi — can enhance the automation of the update process by integrating with Google Workspace services to manage updates more dynamically. It can automate notifications, handle update failures with custom workflows, and ensure compliance across devices.
7. Automated Reporting
Automating the generation of comprehensive reports is essential for understanding device usage, monitoring compliance, and assessing security status across an organization. This automation ensures timely insights into IT infrastructure, helping organizations make informed, data-driven decisions without adding the burden of manual reporting on the team members.
Tools for Implementing Automated Reporting for Google Workspace MDM Best Practices
Google Admin Console — basic reporting features for device management, user activity, and security settings within Google Workspace. It includes reports on account status, device configuration, and security events. No automations are available though.
Google Data Studio — advanced data visualization and reporting capabilities that can be integrated with Google Workspace data. It allows for the creation of customizable dashboards and reports that can be updated in real-time.
Third-party BI and Analytics Tools (e.g., Tableau) — provide robust analytics and business intelligence capabilities, can handle large datasets and complex queries. The downside is that to automate reporting custom scripting is needed.
Zenphi — is a unique tool that can connect data with any viualization tool you’re using (like Tableau or Looker) provide necessary automation capabilities without scripting. It will automate the workflow of generating and distributing reports, sending data to necessary tools, notofying relevant parties about results and more.
Zenphi has already helped to build thousands of workflow automations for Google Workspace, implementing best practices globally. Contact our support team to get a guided automated reporting workflow setup for free!
Empower Your IT Management with Smart Google Workspace MDM Automation in 2025
The seven automation strategies outlined here provide a robust framework for leveraging the full potential of Google Workspace, enhancing security, and streamlining management tasks. By integrating advanced tools like Google Admin Console, Zenphi, and third-party solutions such as Looker, organizations can not only maintain but enhance their operational posture. These automations ensure that your IT environment adapts in real-time, remains secure against evolving threats, and operates with optimal efficiency.
Embrace these automations to transform your Google Workspace environment into a more dynamic, responsive, and secure system that’s ready to meet the challenges of 2025 and beyond.