Table of Contents
Google User Management Pain Point Or Why Automate On-Demand Users Access Approvals
For any company using cloud solutions, user access management is one of the most crucial tasks for system administrators. This is especially true for Google Workspace Admins, where managing user access to various company resources is not just important but often one of the biggest pain points. Balancing the stringent requirements of cybersecurity and compliance with the need to keep the organization running smoothly can be a challenge. After all, if you, as a Google Admin, were to enforce every demand from the cybersecurity team without consideration, it could effectively paralyze the organization’s operations by restricting access too severely.
At first glance, the task seems straightforward: ensuring that the right people have access to the right resources at the right time. And when your organization is small—say, with 5, 10, or even 50 employees—it’s manageable to manually check each user’s access requests for legitimacy. You could even consult the Head of Security for approval and let them bear the consequences of any decisions. However, as your organization scales and the number of employees grows, manually handling all these requests becomes nearly impossible. Manual processes become time-consuming, prone to errors, and difficult to audit, leaving you with little more than email logs to track in the event of a data leak. This inefficiency not only slows down operations but also increases the risk of unauthorized access, potentially leading to security breaches.
The solution in this scenario is to fully automate the on-demand user access request approval process. By using approval workflows automation, you can reduce administrative burdens, free up significant amounts of time, and actually enhance security and compliance. Automated procedures provide a precise log trail that is easy to audit, ensuring that your organization remains secure while still operating efficiently. In this tutorial, we will guide you through setting up automated user access approvals in Google Workspace using Zenphi, the leading solution that allows to automate Google Workspace admin tasks. The flow that we’ll build, will not only simplify the user access management procedure but also ensure that access you provided is properly revoked at the right time.
Google User Management: A Flow To Automate Access Requests Approvals
Set Up Your Zenphi Account
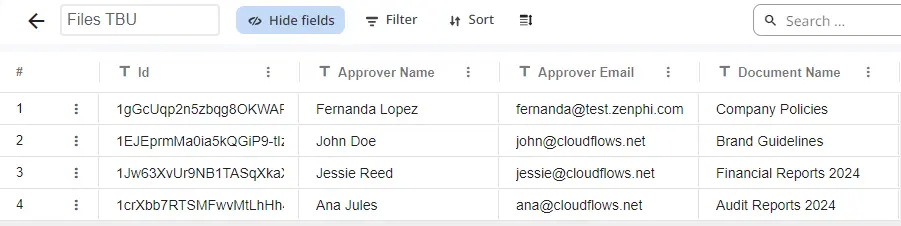
Let’s get started by setting up your Zenphi account. Click here to create your free account. Once you’re in, it’s time to build your first automated flow. In Zenphi, a ‘flow’ is the entire automated process. It consists of a trigger that starts your flow and subsequent actions that represent the steps in your process. For this example, we will use the “Zenphi form trigger,” which ensures that whenever a response is submitted for an access request, it will automatically be sent for approval as soon as possible. Zenphi forms allow users to use a function called “Lookup” which makes it easy to pull information from Zenphi Tables. Here we have created a table with the different documents they can choose from and their file information.
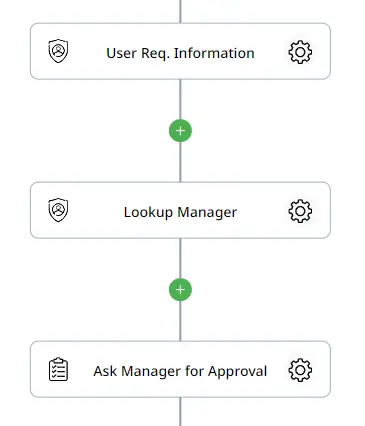
Once the Zenphi flow is configured properly, we will start by adding our actions. The first part of the process involves retrieving the requester’s information, their manager’s information, and finally sending the request for approval.
Action 1: Lookup User Information
By indicating the email of the user, we can retrieve valuable information. Using the Zenphi form’s initiator email, we can easily retrieve the requester’s email address.
Action 2: Lookup Manager
Now that we have the user’s information, we can access their manager’s details using the “Lookup Manager” action. This will provide us with important information like the manager’s full name, email address, and more.
Action 3: Assign Task
We will notify the manager of this request using the “Assign Task” action. Here, we can use the token picker (represented by the chain icon) to include important details like which file was requested, for how long, and more.
Action 4: Conditional Branching
The flow will diverge based on whether the manager approves the request or not. To create these different branches, we use the “If Condition” action, following the true branch only if the request is approved.
- Rejected Request: If the request is rejected, we use the “Send Email (Gmail)” action to notify the requester that their request has been denied, and then terminate the flow.
- Approved Request: If the request is approved, we need to send it to the owner of the file for final approval.
Action 5: Retrieve File Owner Information ("Get Record")
We have previously created a Zenphi Table that contains the file IDs, file owners’ names, and their email addresses. To retrieve this information, we use the “Get Record” action, pulling the relevant fields from the table based on the selected record in the form.
Action 6: Assign Task to File Owner
With this new information, we use the “Assign Task” action again, this time sent to the file owner, indicating that the request has been received and providing any pertinent information.
Action 7: Was the request approved?
Now, once again, the flow will diverge based on whether the owner of the file approves the request or not. And again making use of the “If Condition” action, our flow will follow the true branch only if the request is approved.
- Rejected Request: If the request is rejected, we use the “Send Email (Gmail)” action to notify the requester that their request has been denied, and then terminate the flow.
- Approved Request: If the request is approved, we will begin the process of granting access to the user.
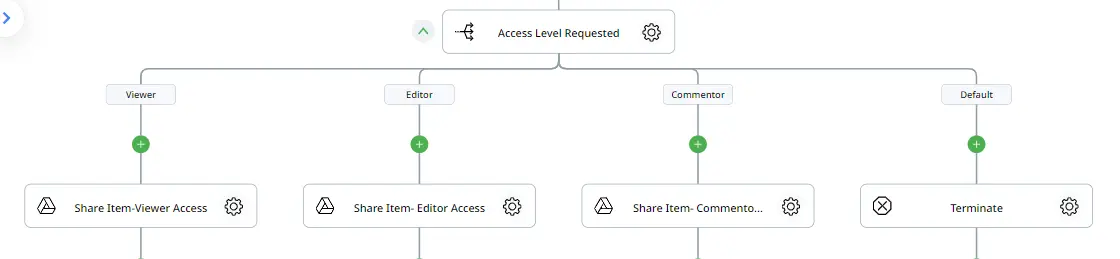
Action 8: Yes — Share Access with the Requester
To share the asset according to the requested access level, we will use a “Switch by Value” action, creating different branches for viewer, editor, and commenter access. In each branch, we will include a “Share Item” action, indicating the correct role based on the branch, retrieving the file ID from our previous “Get Record” action, and adding the user’s email address
Action 9: Yes — Notify the Requester
Now that the user has received access to the asset, we will notify them via email using the “Send Email (Gmail)” action. We will inform the user that they can now access the asset and that their access will be revoked once the selected time has concluded.
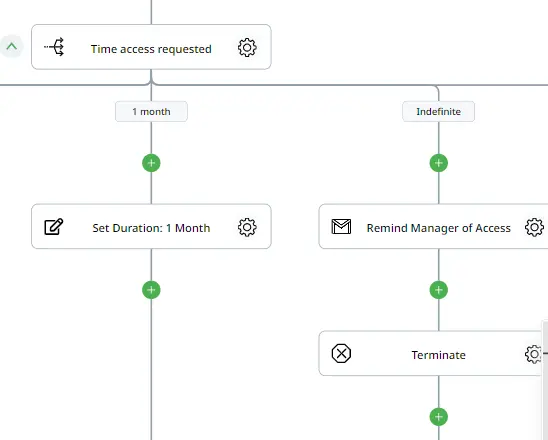
Action 10: Set The Time Access Variable
To properly revoke access to the asset upon the requested date, we will use a variable to store how many days they have requested access.
Using the “Switch by Value” action and subsequently the “Set Variable” action, we will store the selected number of days. However, if they have chosen “Indefinite Time” in the form, we will notify their manager using the “Send Email (Gmail)” action. This will inform the manager that the user will have access to the file until someone manually revokes their access, and then terminate the flow.
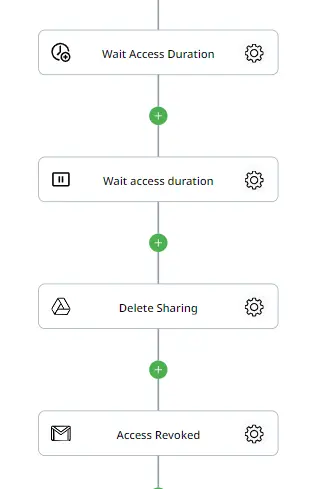
Action 11: Revoke Sharing to the User
To revoke access to the asset when the end access date arrives, we need to pause our flow for a certain time. First, use the “Add Date/Time” action to add the requested days to the current date. Then, configure the “Pause” action to wait until the specific time derived from the previous action. Once our flow reaches the selected time, we will revoke access using the “Delete Sharing” action, which allows sharing to be revoked using the user’s email address.
Action 12: Notify the User of Revoked Access
Once access has been revoked, we will finish our flow by notifying the user via email that they no longer have access to the file. For this, we will use the “Send Email (Gmail)” action one final time.
Testing and Publishing your Flow
And just like that, you have automated your user access approvals in a few easy steps! [Read How To Improve Google Workspace User Management By Automating Role-Based Access Approvals]
This will make it easier to manage any requests, ensuring they’re handled promptly and maintaining the security of your files. Simply save and publish your flow, and it will automatically start whenever an access request is submitted.
Follow This Video Guide
Please follow this video guide to replicate the flow in your organization.