Discover the real daily cost of fragmented security automation in mid-market IT. Includes an infographic and practical guidance for stronger policy execution.
Table of Contents
Security is Rarely a "Tool" Problem—It’s an Execution Problem
For IT leaders – especially, in mid-sized companies — the challenge usually isn’t finding the right tools. It’s finding the time to make them all play nice together. You’ve done the hard work of putting the essentials in place: the identity controls are there, the endpoints are protected, and the playbooks are written. On paper, everything should be running smoothly.
But in reality, the day-to-day feels a bit different. You might notice that:
- Small gaps linger: Access changes don't always happen as fast as they should.
- The "Exception" pile grows: Temporary fixes start feeling a bit too permanent.
- Audits feel like fire drills: Instead of a quick check, they become all-hands-on-deck events.
- Silence is scary: You find yourself wondering if your automations are working, or if they just stopped talking to each other.
It isn’t that your team doesn’t care; it’s that mid-market security lives in a constant state of being “almost automated.” You’re big enough to have complex needs, but too lean to have a dedicated army of engineers to maintain your scripts.
Zenphi supports all scopes of IT Operations automation and enforcement-first workflows for Google Workspace environments—enabling consistent execution without bots, brittle scripts, or automation sprawl. Book a call with automation expert to leaen more.
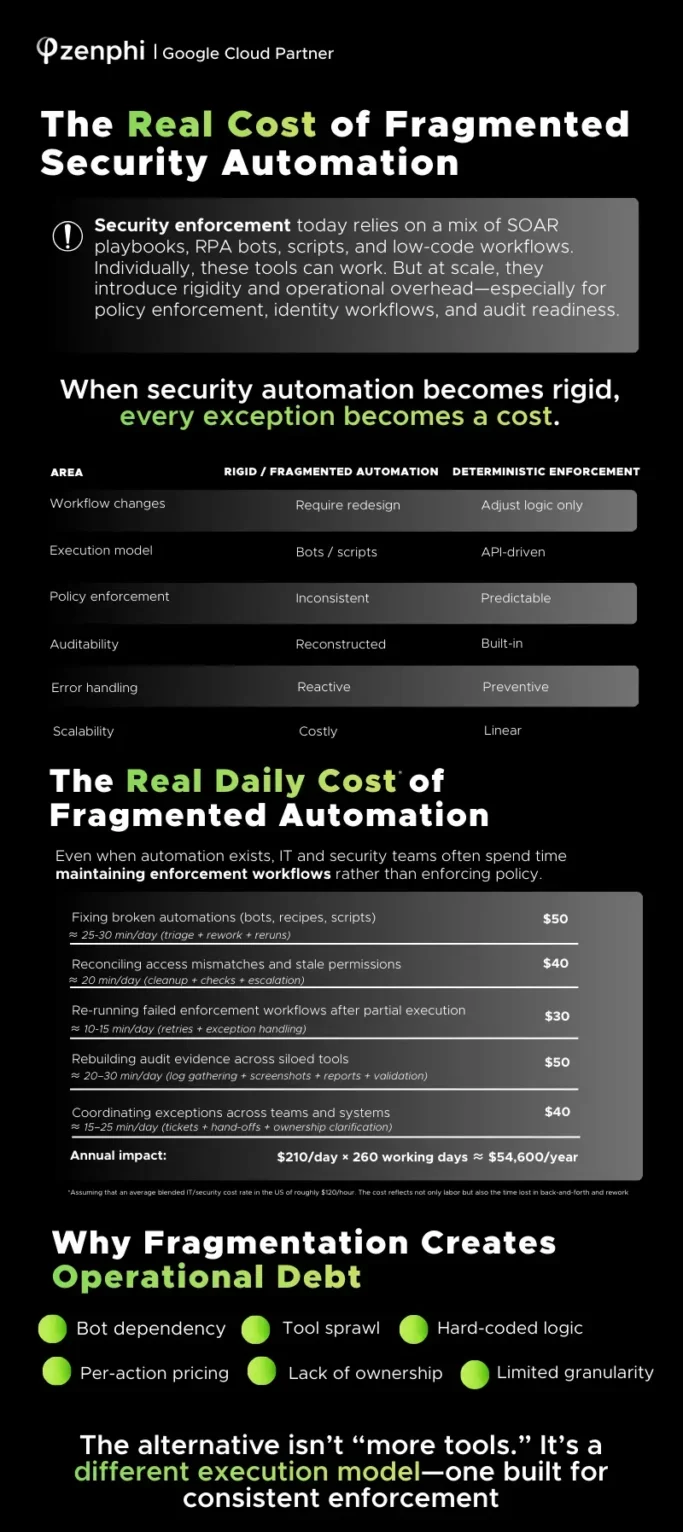
The Real Cost of Security Automation (and Fragmentation)
When we talk about the cost of security automation, we usually think about the price of the software license. But the real cost—the one that actually drains your budget—is operational debt.
When automation is fragmented (relying on brittle bots and custom-coded scripts), every small change in your environment becomes a mini-project. You aren’t just paying for the tool; you’re paying for the “automation tax” that accumulates every day:
- Triage and Rework: Spending nearly 30 minutes a day just fixing broken "recipes" or scripts ($50/day).
- Stale Permissions: Manually reconciling access mismatches that should have been handled by the system ($40/day).
- Audit Fire Drills: Rebuilding evidence after the fact because the data wasn't captured during execution ($50/day).
When you add up these friction points, the annual impact of fragmented automation reaches roughly $54,600 per year. That is money and time that should be going toward growth, not maintenance.
Why "More Tools" Rarely Lowers the Price Tag
The natural instinct is to add another tool to the stack to bridge the gap. But more tools often lead to more exceptions. Complexity doesn’t disappear; it just shifts.
We see this clearly with new challenges like Generative AI. It only takes one employee pasting sensitive data into a public chatbot to create a risk. You don’t need a new tool to detect that; you need a reliable way to enforce your policies across the entire digital workspace, every single time.
The default reaction is often a new script or another manual ticket, but that just adds to the fragmentation. The real shift happens when you move from rigid automation to deterministic enforcement.
Moving to an "Enforcement-First" Model
In mid-market IT, success isn’t about having the most tools—it’s about having the most predictable execution. You need an execution layer that focuses on:
- Event-Driven Actions: Replacing manual tickets with workflows that trigger the moment a hire is made or a role changes.
- Deterministic Logic: No "works until it doesn't" scripts—just predictable, API-driven actions across all your systems.
- Built-in Governance: Exceptions shouldn't be workarounds; they should be routed through structured approvals that are recorded automatically.
- Audit-Ready Execution: Capturing a record of what happened as it happens, so you never have to "reconstruct" a log again.
How Zenphi Bridges the Gap
Zenphi acts as this missing execution layer. It isn’t another security monitor or a heavy enterprise platform. It’s an operations automation layer built to make your existing Google Workspace and cloud environments execute predictably.
By standardizing workflows—from user lifecycle management to approval workflows to policy exception gating—you can finally close the gap between your security intent and what actually happens on a Tuesday morning.
As we stepped into 2026, the goal isn’t just to have a better policy on a shelf. It’s to ensure that policy is actually happening—accurately, consistently, and without the hidden overhead of manual rework.
Download The Google Cloud Cybersecurity Forecast-2026