Over the past year, a mix of independent research and Zenphi customer data has revealed a clear trend: the problem isn’t visibility—it’s enforcement. This article outlines the top security and shadow IT trends shaping Google Workspace environments and how teams are adapting through policy-based automation.
Table of Contents
Google Workspace has become the backbone of productivity for thousands of organizations—but with that scale comes complexity. From Gmail and Drive to OAuth and Chrome extensions, IT teams are expected to monitor and secure a constantly expanding SaaS environment.
Over the past year, a mix of independent research and Zenphi customer data has revealed a clear trend: the problem isn’t visibility—it’s enforcement. This article outlines the top security and shadow IT trends shaping Google Workspace environments and how teams are adapting through policy-based automation, leveraging AI for IT operations.
Shadow IT Is Not the Enemy—But It Is the Weakest Link
When people talk about Shadow IT, they often make it sound malicious. In reality, it’s not.
Shadow IT is usually just your employees doing what they need to do to get their jobs done: installing a Chrome extension that helps them organize tabs, connecting a time-tracking app to their Calendar, or forwarding emails to a personal address so they don’t miss anything while traveling.
But even if the intent is harmless, the consequences rarely are — especially for the security workflows.
In Google Workspace environments, shadow IT often bypasses the standard security controls in place for Gmail, Drive, OAuth, and Chrome — giving third-party tools access to sensitive company data without oversight. And in most companies, this isn’t an isolated issue — it’s an everyday occurrence.
Zenphi is the leading automation platforms for teams utilizing Google Workspace as their main productivity environment. Zenphi helps to build a wide range of IT operations automations — from Shadow IT detection to standard Google admin tasks automation. Book a call to learn more.
How Big Is the Problem?
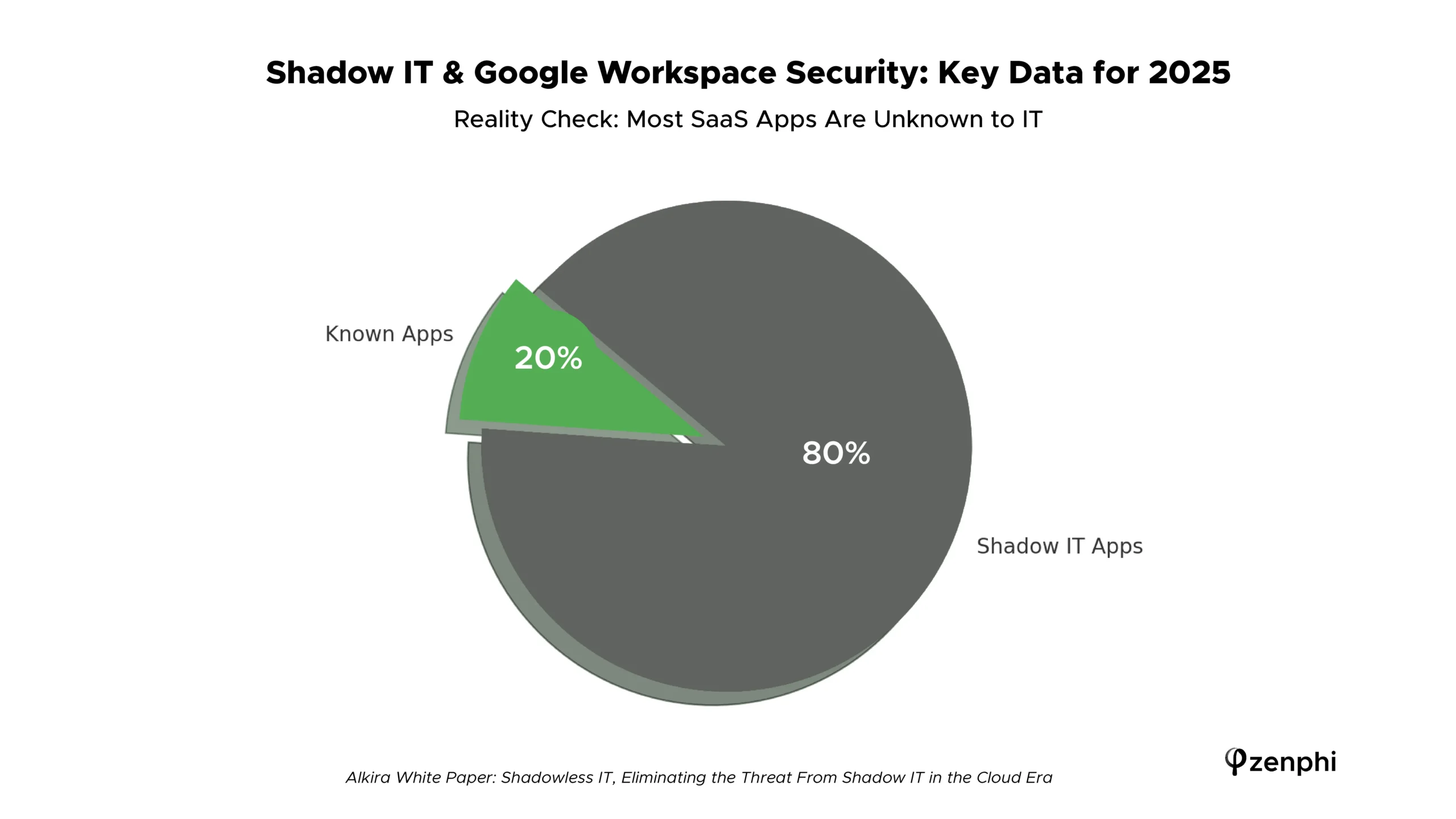
Recent independent research paints a sobering picture. For instance, 42% of the average company’s apps are “shadow IT” (around 78 out of 187 apps) according to one analysis, and according to Alkira’s white paper: Shadowless IT, only 20% of apps being installed by employees, are known to the IT department.
This problem is especially relevant to large enterprises — as they often dramatically underestimate their cloud footprint: one report found companies had about 975 unknown cloud services in use versus only 108 known to IT.
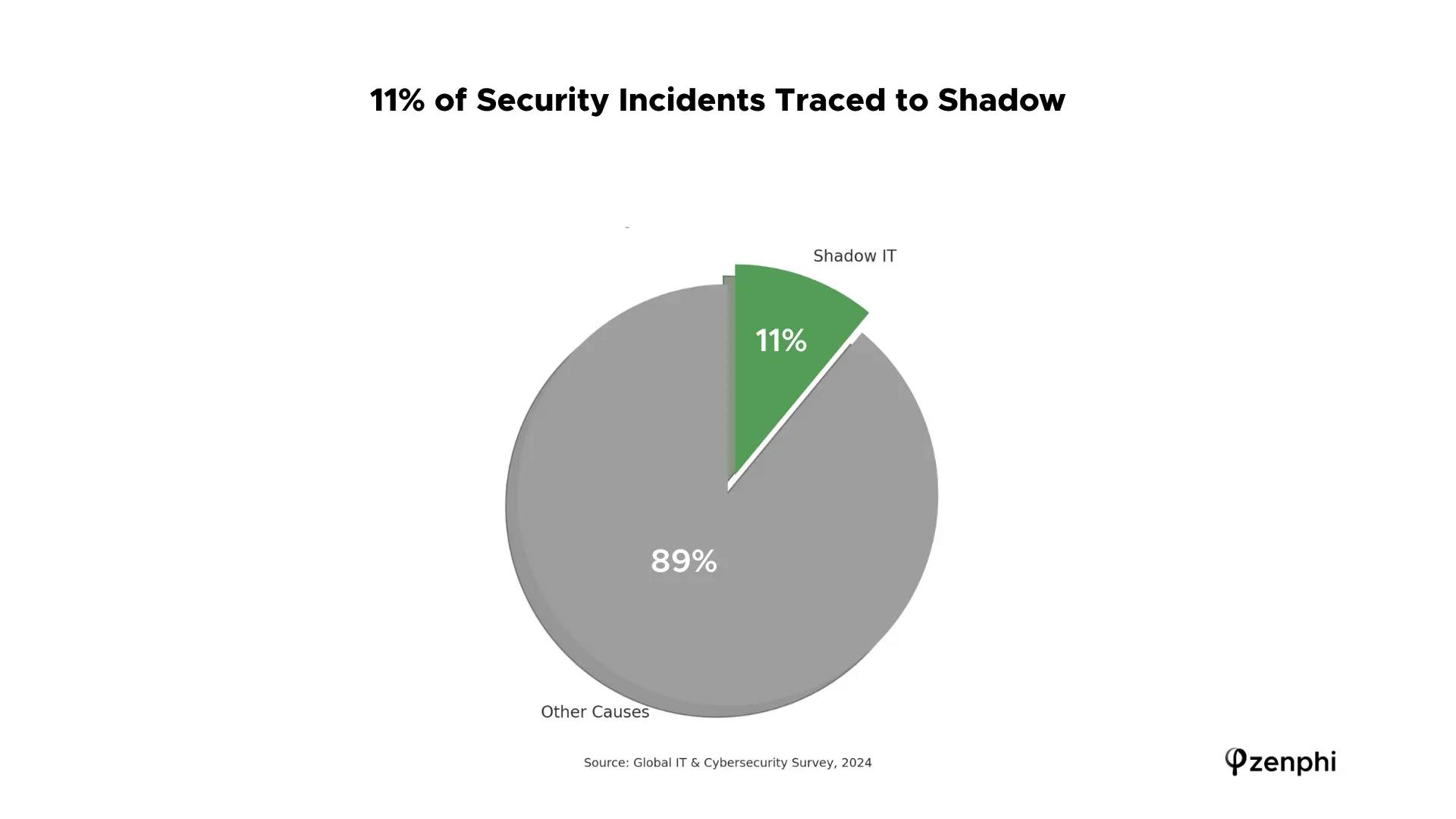
This proliferation of unvetted apps leads to real security incidents – 85% of businesses worldwide reported cyber incidents in the past two years, and roughly 11% of those were directly linked to unauthorized shadow IT usage (Source: Infosecurity Magazine).
In fact, nearly one in two cyberattacks can be traced back to shadow IT vulnerabilities, with remediation costs averaging $4.2 million per incident (Source: Cost Of Data Breach Report, 2024). Such findings underscore how widespread and risky unsanctioned SaaS has become in the cloud era.
Challenges with Manual Security Enforcement
IT teams are struggling to keep pace with the surge of SaaS and shadow IT.
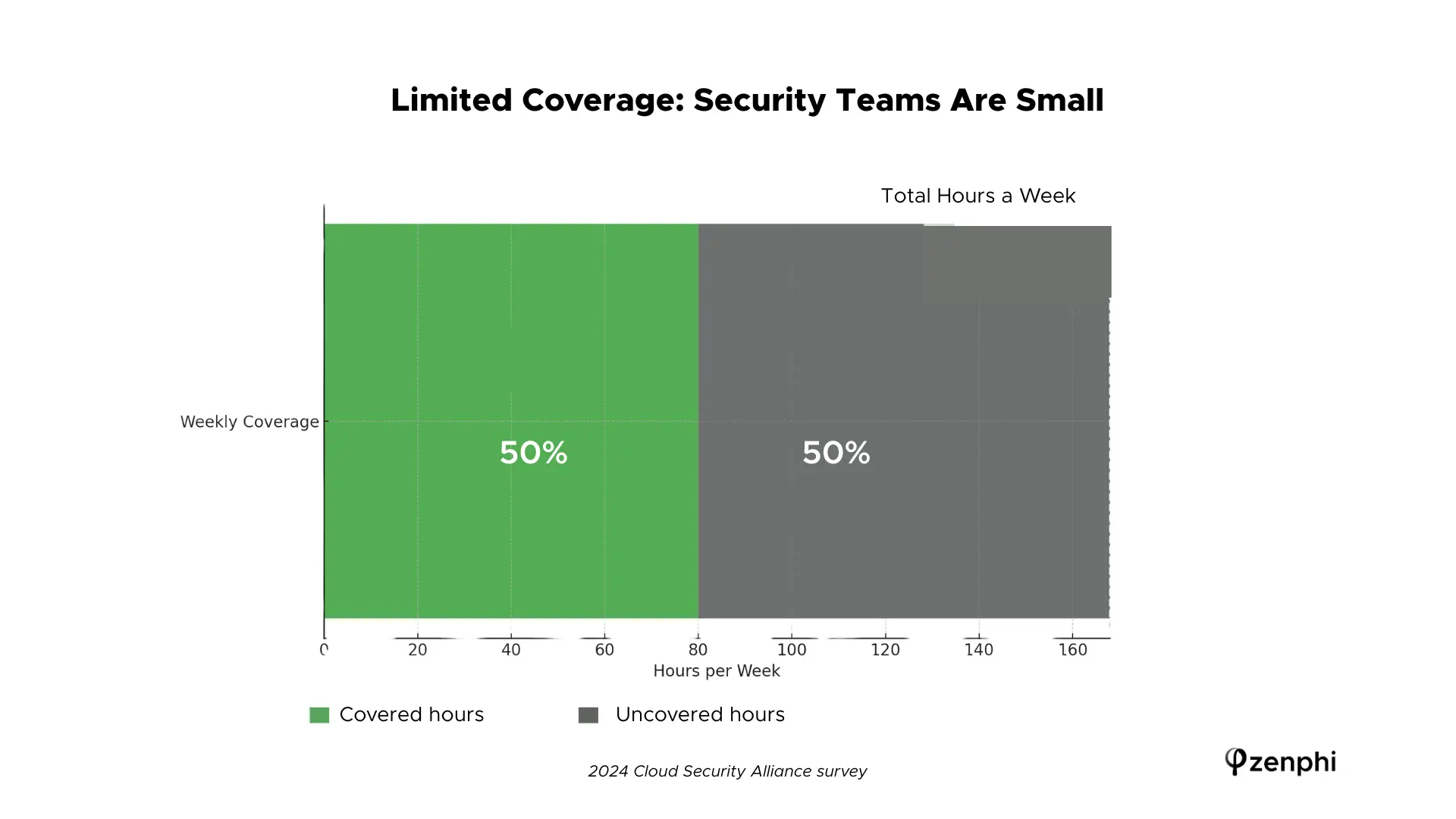
Many organizations simply lack the bandwidth to manually monitor and secure every app employees adopt. A 2024 Cloud Security Alliance survey highlights that while 70% of organizations now have a dedicated SaaS security team, these teams are typically just one or two people. This means coverage gaps – with only two staffers, there are 88 hours a week when no one is actively watching SaaS security.
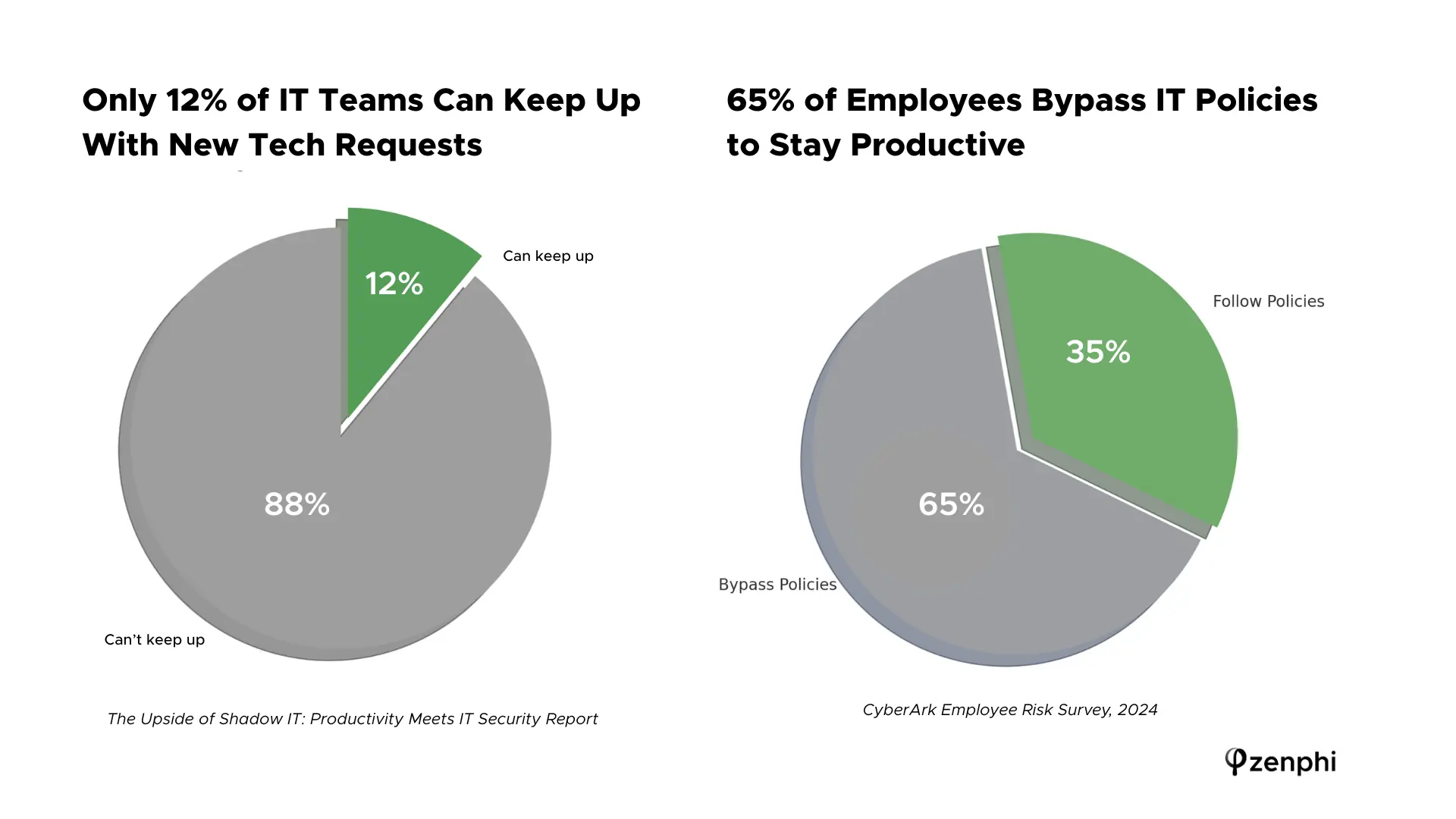
Maintaining visibility into third-party app activity is especially difficult; monitoring for suspicious behavior across hundreds of apps is cited as a significant challenge in mature SaaS environments. The result is that IT often doesn’t know about many apps or integrations employees use. Only 12% of IT departments report being able to keep up with all new tech requests, and as much as 65% of employees admit they bypass IT policies when those policies hinder productivity (Source: Gartner Security & Risk Management Summit Report)
Unfortunately, this gap between IT oversight and employee behavior leaves many organizations flying blind on security. As Google’s own global survey found, 56% of decision-makers say even they themselves don’t always follow their company’s IT policies, and nearly half believe that using unsanctioned tools is “completely safe” (Source: Google Workspace Newsletter, February 2025 ). Clearly, relying on manual enforcement and trust alone is proving insufficient.
That’s exactly what Gordon Food Service IT team was facing when they went all in with approval workflows automation. Read more about their success in this case study.
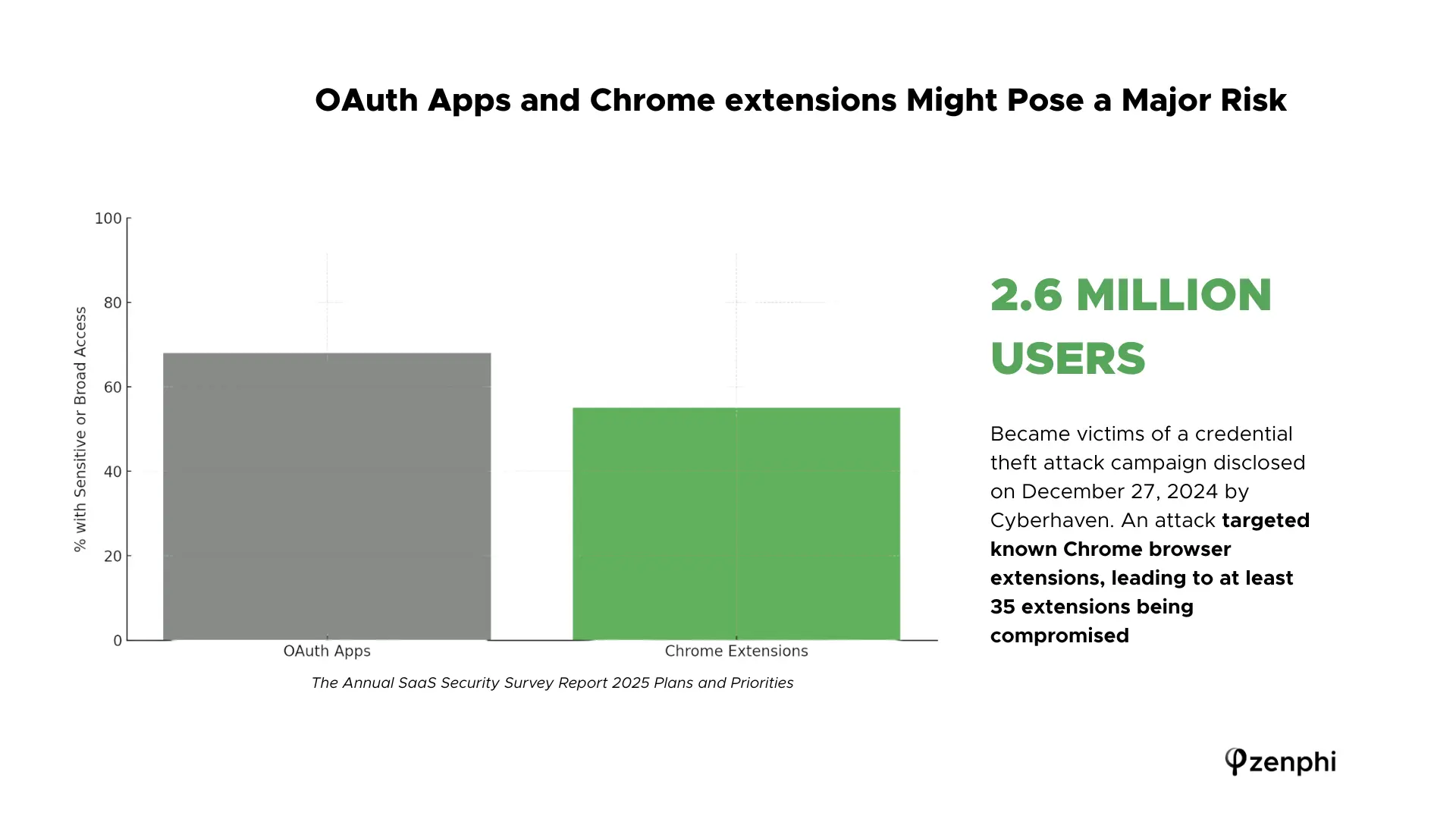
OAuth App & Chrome Extension Risks in Google Workspace
Google Workspace admins face particular shadow IT threats from third-party OAuth apps and Chrome extensions. Employees routinely grant third-party apps access to corporate Google accounts (Gmail, Drive, etc.) via OAuth, often without IT’s knowledge. Each OAuth consent can introduce a backdoor: apps frequently request broad permissions – such as the ability to read or even send emails on a user’s behalf – creating obvious abuse potential. Worse, it’s almost impossible to trace which apps have been granted permissions across an organization by manual means.
One careless click by an employee on a malicious Gmail add-on can thus put domain-wide data at risk. Chrome browser extensions pose a similar concern. The Chrome Web Store hosts over 200,000 extensions, many built for consumers and granted extensive privileges. In late 2024, security researchers uncovered a campaign that compromised two dozen popular Chrome extensions, potentially exposing 2.5 million users’ data (Source: The Hacher News, December 2024). Some extensions surreptitiously harvested sensitive info like session cookies and credentials. Because users rarely scrutinize extension permissions, a single rogue extension can quietly siphon data or inject malware. Google Workspace itself was identified in a 2024 industry survey as one of the top five business applications that are most challenging to secure.
This is largely due to the ecosystem of connected apps and extensions around it. All these factors highlight the delicate position of IT admins: tasked with protecting Gmail, Drive, and Chrome usage, yet often lacking automated tools to gain full visibility and control over the sprawl of third-party add-ons.
The Rise of IT Workflow Automation
To combat these challenges, organizations are increasingly turning to integrated security workflows automation. There is a strong industry push toward automating routine IT operations and security tasks that were once done manually.
This, of course, reflects a broader trend: over 80% of executives report they’ve accelerated process automation efforts and remote-work tooling in the past couple years (Source: The Future Of Jobs Report).
In practice, automation is being applied to SaaS management and security in many ways – from user access control automation, to auto-detecting new SaaS sign-ups, to automatically revoking risky app permissions, to streamlined user lifecycle management workflows. The expected benefits are twofold: relieving overextended IT teams from tedious manual oversight, and reducing human error (still the cause of ~90% of security breaches). Surveys show that business leaders believe automating tasks could save each employee hundreds of hours per year while curbing costs (Source: Work Market Insight Report).
Smarter Not More
In the security arena, automation definitely helps by monitoring systems continuously and enforcing policies in real-time.
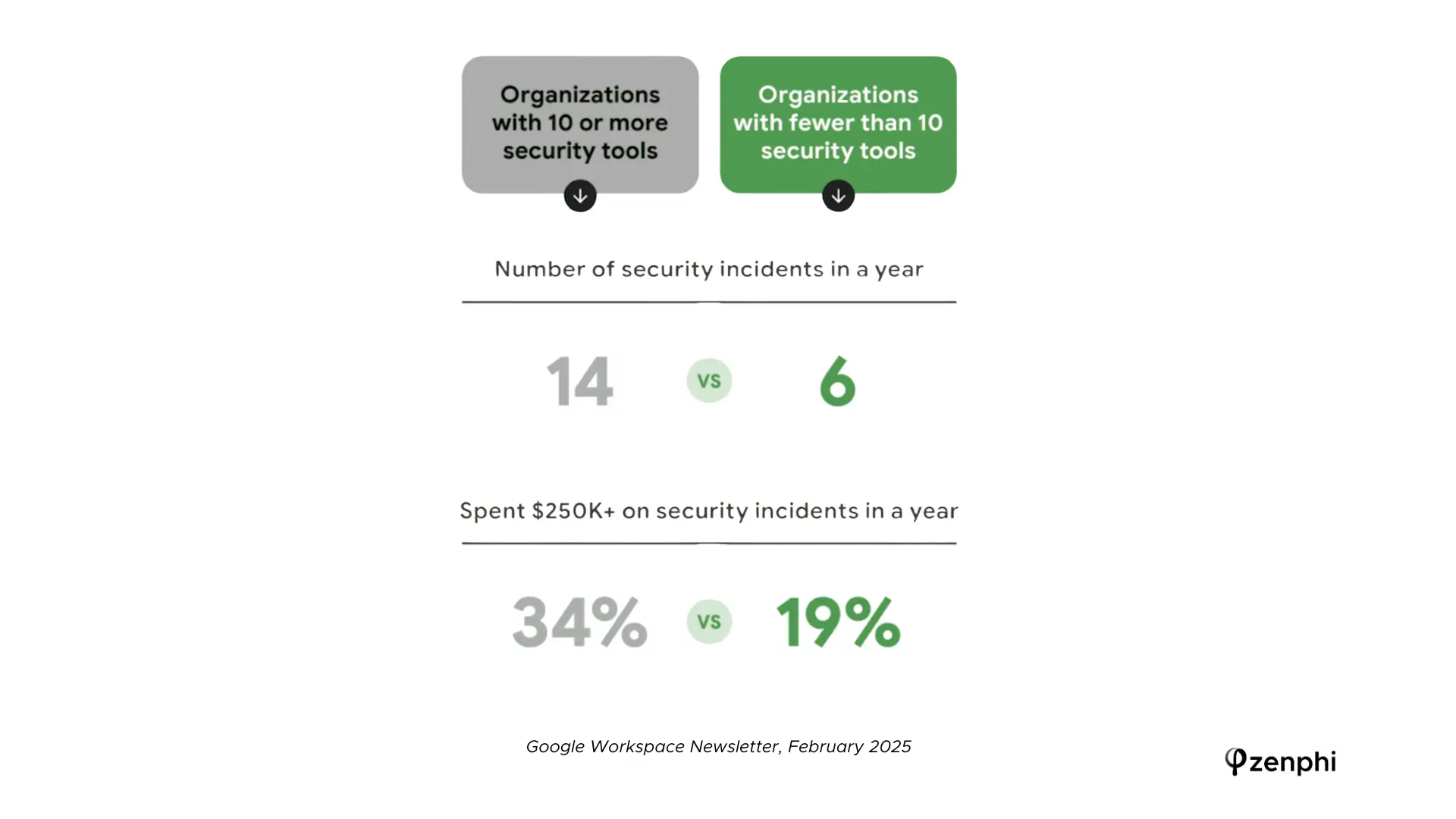
However, does it mean that companies should impliment more checks and balances to track what, when and by whom are being installed or downloaded? In other words, does having more security tools or paying more for them lead to better outcomes?
It doesn’t seam this way. Google’s 2025 Security Survey found that organizations with 10 or more security tools actually saw higher incident rates – an indicator that piling on point solutions without coordination can backfire (Source: Google Workspace Newsletter, February 2025).
The takeaway is that smarter, not just more, security is needed. Forward-leaning IT teams are therefore consolidating and automating: using fewer, more “secure-by-design” platforms and scripting away repetitive admin tasks. This reduces the attack surface and ensures critical things (like OAuth app reviews, Chrome extension whitelists, or Gmail DLP scans) happen automatically rather than on an ad-hoc basis.
From Control to Clarity: Why Simpler Workflows Get Followed
The evidence suggests that it’s not the number of security tools that drives better outcomes—it’s whether people actually follow the processes those tools are meant to support.
And that’s where most shadow IT begins: not with bad actors, but with good intentions and unclear paths.
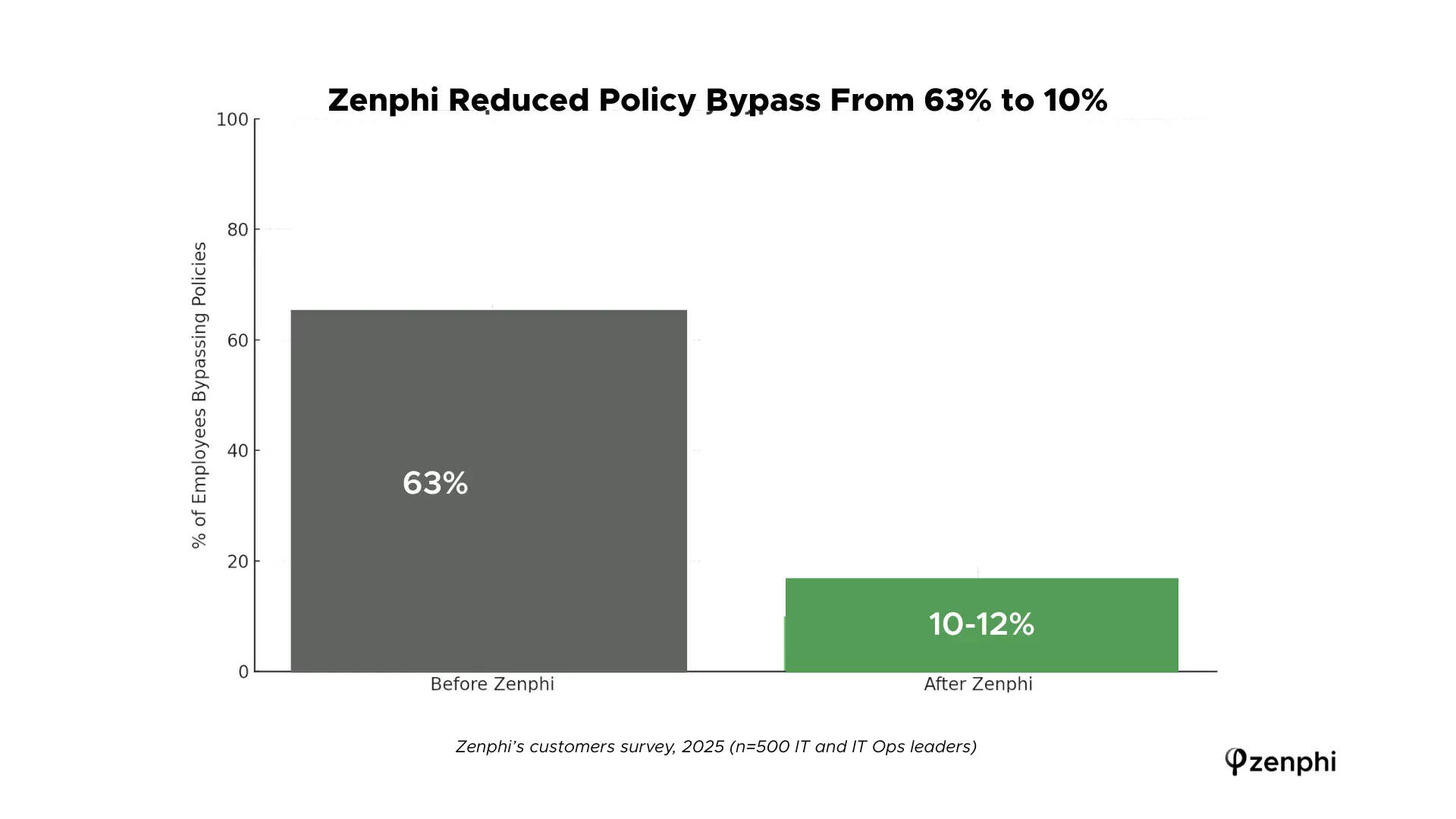
In our 2025 survey of over 500 IT and operations leaders across Zenphi’s customer base, we asked one simple question:
— How often did employees bypass IT policies before and after implementing approval workflows for things like app access, mailbox aliases, or Chrome extensions?
The results were striking. Before automation 63% of employees admitted to bypassing IT policies for the sake of speed or convenience. After introducing automated approval workflows with Zenphi that number dropped to just 10%.
This wasn’t because stricter rules were put in place. In most cases, the policies stayed exactly the same. What changed was clarity—employees were given a faster, simpler, and more secure way to get what they needed. The policy path became the easiest path.
The implication is powerful: most people don’t want to bypass IT—they just want to avoid the bottlenecks. And when you remove the bottlenecks, compliance follows.
Visibility Is the Start — Automation Is the Difference
From shadow IT to stretched-thin admin teams, the challenges around Google Workspace security aren’t going away. In fact, they’re accelerating as more apps, more endpoints, and more users enter the fold.
But the answer isn’t to throw more tools at the problem.
The most effective IT teams we’ve seen aren’t spending more—they’re spending smarter. They’re shifting away from spreadsheets and helpful but hardly scalable Apps Script, toward policy-driven workflows that enforce security automatically, across email, apps, groups, and file sharing.
They’re consolidating where possible, automating where practical, and designing processes that people actually follow.
If you’re ready to go from audit fatigue to scalable enforcement, there’s a growing body of evidence—and real-world examples—showing that automation is the way forward.